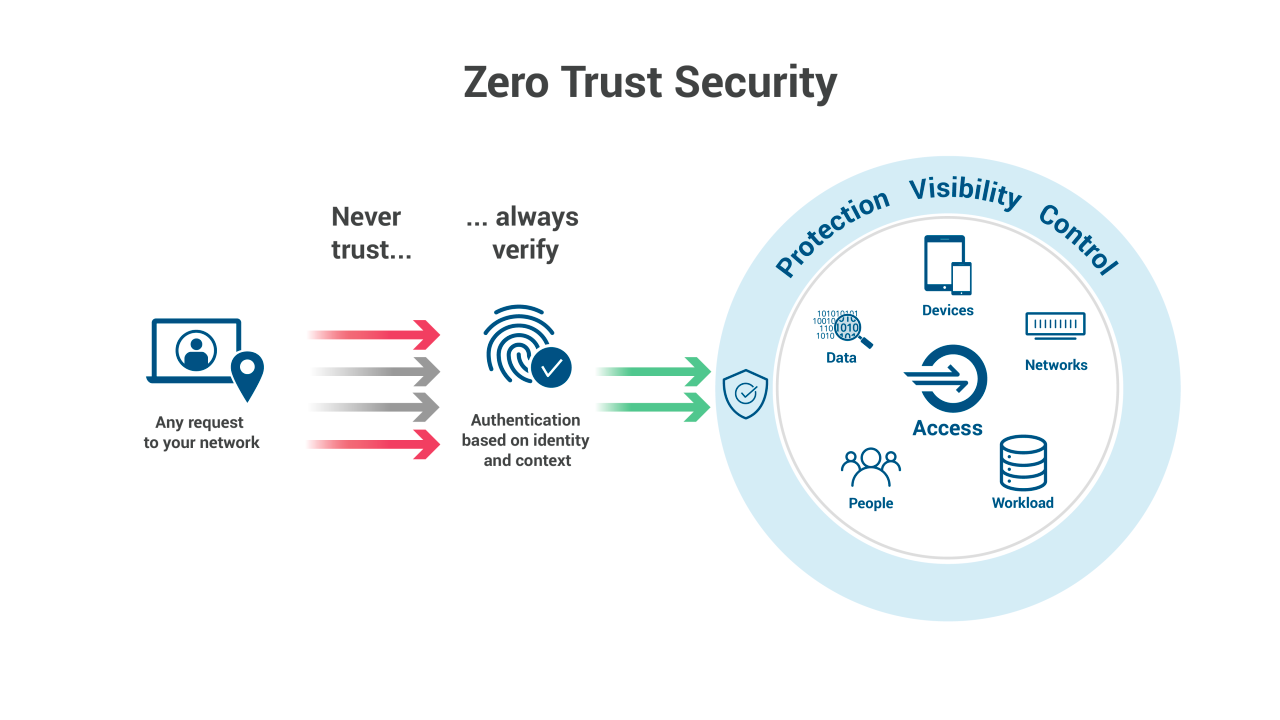
What if every access request was treated with suspicion, regardless of where it came from? That’s the foundation of Zero Trust Architecture, a modern approach to cybersecurity that is becoming increasingly vital in today’s digital world.
Why Zero Trust Is Essential
In a fast-evolving tech landscape, especially in vibrant tech communities like Lagos, Zero Trust is crucial for safeguarding against both external and internal threats. Traditional security models often fail to protect against advanced attacks because they assume that once inside the network, users and devices are inherently safe. Zero Trust challenges this assumption by ensuring that every request is scrutinized, regardless of its origin.
This model is particularly relevant for modern businesses where remote work and cloud computing are prevalent. By enforcing strict access controls and continuous monitoring, Zero Trust helps prevent unauthorized access and data breaches, making it a vital component of a robust cybersecurity strategy.
Implementing Zero Trust
Adopting Zero Trust involves several practical steps. First, you need to identify and protect your critical assets. Next, segment your network to limit the impact of potential breaches. Implement multi-factor authentication (MFA) and ensure that users only have access to the resources they need. Regularly monitor and analyze user behavior to detect any anomalies.
For businesses in Lagos, integrating Zero Trust solutions can enhance security by providing comprehensive visibility and control over network access. These solutions help maintain a secure environment even as technology and work practices evolve.
Conclusion
Zero Trust Architecture is an essential framework for modern cybersecurity, offering a proactive approach to protecting your digital assets. By implementing Zero Trust, businesses can safeguard against advanced threats and ensure that their security measures are both effective and adaptive.
Ready to enhance your cybersecurity knowledge? Explore our courses on Zero Trust Architecture and other advanced security strategies. Visit our website to find the perfect course for your needs and start strengthening your cybersecurity defenses today!